Cisco ASA 設定覚書
検証環境

設定例
リモートアクセス設定
SSH 接続設定
ciscoasa(config)# username admin password cisco privilege 15 ciscoasa(config)# aaa authentication ssh console LOCAL ciscoasa(config)# ssh 0 0 management ciscoasa(config)# ssh timeout 10 ciscoasa(config)# crypto key generate rsa general-keys modulus 1024 noconfirm
HA 設定
Primary 側インターフェース設定
ciscoasa(config)# interface gigabitEthernet 0/0 ciscoasa(config-if)# nameif outside ciscoasa(config-if)# ip address 192.168.10.251 255.255.255.0 standby 192.168.10.252 ciscoasa(config-if)# int gigabitEthernet 0/0 ciscoasa(config-if)# nameif inside ciscoasa(config-if)# ip address 192.168.20.251 255.255.255.0 standby 192.168.20.252 ciscoasa(config-if)# exit
Primary 側 Failover 設定
ciscoasa(config)# failover lan unit primary ciscoasa(config)# failover lan interface failover GigabitEthernet0/2 ciscoasa(config)# failover interface ip failover 10.1.1.1 255.255.255.0 standby 10.1.1.2 ciscoasa(config)# failover link state GigabitEthernet0/3 ciscoasa(config)# failover interface ip state 10.1.2.1 255.255.255.0 standby 10.1.2.2
Secondary 側 Failover 設定
ciscoasa(config)# failover lan interface failover GigabitEthernet0/2 ciscoasa(config)# failover interface ip failover 10.1.1.1 255.255.255.0 standby 10.1.1.2
Primary 側インターフェース有効化
ciscoasa(config-if)# interface gigabitEthernet 0/0 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# interface gigabitEthernet 0/1 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# interface gigabitEthernet 0/2 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# interface gigabitEthernet 0/3 ciscoasa(config-if)# no shutdown
Secondary 側インターフェース有効化
ciscoasa(config-if)# interface gigabitEthernet 0/0 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# interface gigabitEthernet 0/1 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# interface gigabitEthernet 0/2 ciscoasa(config-if)# no shutdown ciscoasa(config-if)# interface gigabitEthernet 0/3 ciscoasa(config-if)# no shutdown
Primary 側 Failover 有効化
ciscoasa(config)# failover
Secondary 側 Failover 有効化
ciscoasa(config)# failover
Failover 状態確認
ciscoasa# show failover state
State Last Failure Reason Date/Time
This host - Primary
Active None
Other host - Secondary
Standby Ready None
====Configuration State===
Sync Done - STANDBY
====Communication State===
Mac set
ファイアウォール設定
アクセスリストの設定(outside から inside への icmp/http/https 許可)
ciscoasa(config)# object-group service DM_INLINE_SERVICE_1 ciscoasa(config-service-object-group)# service-object icmp ciscoasa(config-service-object-group)# service-object tcp destination eq www ciscoasa(config-service-object-group)# service-object tcp destination eq https ciscoasa(config)# access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_1 192.168.10.0 255.255.255.0 192.168.20.0 255.255.255.0 ciscoasa(config)# access-group outside_access_in in interface outside
ポートスキャン試験(Client→Web Server)
Nmap によるポートスキャン
[root@hostname ~]# nmap -v -sS 192.168.20.101 Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2014-02-21 08:41 PST DNS resolution of 1 IPs took 0.01s. Initiating SYN Stealth Scan against 192.168.20.101 [1680 ports] at 08:41 Discovered open port 80/tcp on 192.168.20.101 The SYN Stealth Scan took 25.15s to scan 1680 total ports. Host 192.168.20.101 appears to be up ... good. Interesting ports on 192.168.20.101: Not shown: 1678 filtered ports PORT STATE SERVICE 80/tcp open http 443/tcp closed https Nmap finished: 1 IP address (1 host up) scanned in 25.336 seconds Raw packets sent: 3364 (147.996KB) | Rcvd: 7 (322B)
Remote Access VPN 設定
ASA 設定
ciscoasa(config)# ip local pool pool 172.16.1.1-172.16.1.10 mask 255.255.255.0 ciscoasa(config)# webvpn ciscoasa(config-webvpn)# enable outside ciscoasa(config-webvpn)# anyconnect image disk0:/anyconnect-linux-64-3.1.0515$ ciscoasa(config-webvpn)# anyconnect enable ciscoasa(config-webvpn)# tunnel-group-list enable ciscoasa(config-webvpn)# group-policy DfltGrpPolicy attributes ciscoasa(config-group-policy)# vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-clien$ ciscoasa(config-group-policy)# group-policy GroupPolicy_WebVPN internal ciscoasa(config)# group-policy GroupPolicy_WebVPN attributes ciscoasa(config-group-policy)# wins-server none ciscoasa(config-group-policy)# dns-server value 8.8.8.8 ciscoasa(config-group-policy)# vpn-tunnel-protocol ssl-client ciscoasa(config-group-policy)# default-domain none ciscoasa(config-group-policy)# tunnel-group WebVPN type remote-access ciscoasa(config)# tunnel-group WebVPN general-attributes ciscoasa(config-tunnel-general)# address-pool pool ciscoasa(config-tunnel-general)# default-group-policy GroupPolicy_WebVPN ciscoasa(config-tunnel-general)# tunnel-group WebVPN webvpn-attributes ciscoasa(config-tunnel-webvpn)# group-alias WebVPN enable
Client から HTTPS 接続

Link から AnyConnect Secure Mobility Client をダウンロード
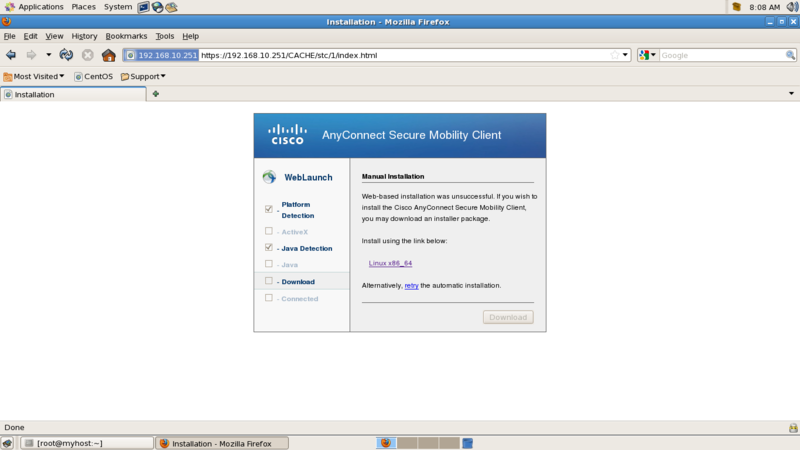
vpnsetup.sh. ファイルをオープン

Could not open the file /tmp/vpnsetup.sh. エラー

vpnsetup.sh 実行
[root@hostname ~]# chmod 755 vpnsetup.sh [root@hostname ~]# ./vpnsetup.sh Installing Cisco AnyConnect Secure Mobility Client... Extracting installation files to /tmp/vpn.G11283/vpninst502577000.tgz... Unarchiving installation files to /tmp/vpn.G11283... Starting Cisco AnyConnect Secure Mobility Client Agent... Done!
Cisco AnyConnect Secure Mobility Client 起動

アドレスを設定し[Connect]

Group、Username、Passoword を設定し[Connect]

WebVPN 接続確認(ASA)
ciscoasa# show vpn-sessiondb anyconnect Session Type: AnyConnect Username : admin Index : 177 Assigned IP : 172.16.1.1 Public IP : 192.168.10.101 Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel License : AnyConnect Premium Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)RC4 DTLS-Tunnel: (1)AES128 Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)SHA1 Bytes Tx : 8258 Bytes Rx : 782 Group Policy : GroupPolicy_WebVPN Tunnel Group : WebVPN Login Time : 04:11:17 UTC Fri Feb 21 2014 Duration : 0h:00m:05s Inactivity : 0h:00m:00s VLAN Mapping : N/A VLAN : none Audt Sess ID : c0a814fb000b10005306d1e5 Security Grp : 0
WebVPN 接続確認(Client)
[root@hostname ~]# ifconfig cscotun0 cscotun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 inet addr:172.16.1.1 P-t-P:172.16.1.1 Mask:255.255.255.0 UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1406 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:500 RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
以上