ASA と VyOS で IPsec
VyOS とは
VyOS は Vyattaの無償版である Vyatta Core よりフォークされたオープンソースのネットワーク OS です。
Cisco の ASA(HA 構成)と VyOS 間で IPsec を確立する際の設定例になります。
検証環境
- VyOS1.1.7 及び、CentOS6.8 を VMware Workstation 上に構築
- VMware ESXi5.5 を VMweare Workstation 上に構築し、ESXi5.5 上に ASAv を構築*1
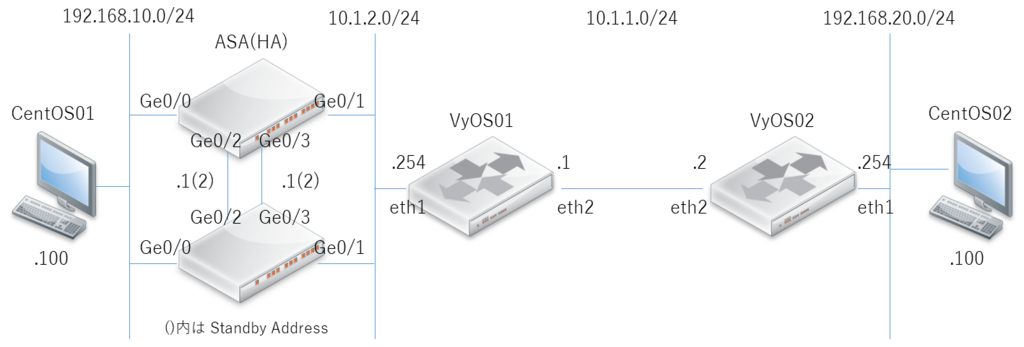
ASA 設定例
HA 関連の最終設定
※HA の具体的な設定方法は、こちらをご参照ください。
<...snip...> interface GigabitEthernet0/0 nameif inside security-level 100 ip address 192.168.10.1 255.255.255.0 standby 192.168.10.2 ! interface GigabitEthernet0/1 nameif outside security-level 0 ip address 10.1.2.1 255.255.255.0 standby 10.1.2.2 ! interface GigabitEthernet0/2 description LAN Failover Interface ! interface GigabitEthernet0/3 description STATE Failover Interface <...snip...> failover failover lan interface failover GigabitEthernet0/2 failover link state GigabitEthernet0/3 failover interface ip failover 172.16.1.1 255.255.255.0 standby 172.16.1.2 failover interface ip state 172.16.2.1 255.255.255.0 standby 172.16.2.2 <...snip...>
HA の確認
ciscoasa# show failover Failover On Failover unit Primary Failover LAN Interface: failover GigabitEthernet0/2 (up) Unit Poll frequency 1 seconds, holdtime 15 seconds Interface Poll frequency 5 seconds, holdtime 25 seconds Interface Policy 1 Monitored Interfaces 3 of 61 maximum Version: Ours 9.2(0)2, Mate 9.2(0)2 Last Failover at: 02:57:55 UTC Sep 19 2016 This host: Primary - Active Active time: 27 (sec) slot 0: empty Interface inside (192.168.10.1): Normal (Monitored) Interface outside (10.1.2.1): Normal (Monitored) Interface management (192.168.1.101): Normal (Monitored) Other host: Secondary - Standby Ready Active time: 12455 (sec) Interface inside (192.168.10.2): Normal (Monitored) Interface outside (10.1.2.2): Normal (Monitored) Interface management (192.168.1.102): Normal (Monitored) <...snip...>
ルートの設定
route outside 10.1.1.0 255.255.255.0 10.1.2.254 1 route outside 192.168.20.0 255.255.255.0 10.1.2.254 1
IPsec の設定
IKE ポリシーの定義及び有効化
crypto ikev1 policy 10 authentication pre-share encryption aes hash sha group 2 lifetime 86400 crypto ikev1 enable outside
Tunnel Group (LAN-to-LAN プロファイル)の作成
tunnel-group 10.1.1.2 type ipsec-l2l tunnel-group 10.1.1.2 ipsec-attributes ikev1 pre-shared-key cisco
セレクタ ACL の設定
object-group network local-network network-object 192.168.10.0 255.255.255.0 object-group network remote-network network-object 192.168.20.0 255.255.255.0 access-list asa-router-vpn extended permit ip object-group local-network object-group remote-network
NAT 除外設定
nat (inside,outside) source static local-network local-network destination static remote-network remote-network no-proxy-arp route-lookup
IKE トランスフォーム設定
crypto ipsec ikev1 transform-set ESP-AES-SHA esp-aes esp-sha-hmac
Crypto MAP の設定とインターフェースへの適用
crypto map outside_map 10 match address asa-router-vpn crypto map outside_map 10 set peer 10.1.1.2 crypto map outside_map 10 set ikev1 transform-set ESP-AES-SHA crypto map outside_map interface outside
IPsec 関連の最終設定
<...snip...> object-group network local-network network-object 192.168.10.0 255.255.255.0 object-group network remote-network network-object 192.168.20.0 255.255.255.0 access-list asa-router-vpn extended permit ip object-group local-network object-group remote-network <...snip...> nat (inside,outside) source static local-network local-network destination static remote-network remote-network no-proxy-arp route-lookup <...snip...> crypto ipsec ikev1 transform-set ESP-AES-SHA esp-aes esp-sha-hmac crypto map outside_map 10 match address asa-router-vpn crypto map outside_map 10 set pfs crypto map outside_map 10 set peer 10.1.1.2 crypto map outside_map 10 set ikev1 transform-set ESP-AES-SHA crypto map outside_map 10 set security-association lifetime seconds 28800 crypto map outside_map interface outside crypto ikev1 enable outside crypto ikev1 policy 10 authentication pre-share encryption aes hash sha group 2 lifetime 86400 <...snip...> tunnel-group 10.1.1.2 type ipsec-l2l tunnel-group 10.1.1.2 ipsec-attributes ikev1 pre-shared-key *****
IPsec の確認
ciscoasa# show crypto isakmp sa IKEv1 SAs: Active SA: 1 Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey) Total IKE SA: 1 1 IKE Peer: 10.1.1.2 Type : L2L Role : initiator Rekey : no State : MM_ACTIVE ciscoasa# show crypto ipsec sa interface: outside Crypto map tag: outside_map, seq num: 10, local addr: 10.1.2.1 access-list asa-router-vpn extended permit ip 192.168.10.0 255.255.255.0 192.168.20.0 255.255.255.0 local ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.20.0/255.255.255.0/0/0) current_peer: 10.1.1.2 #pkts encaps: 21281, #pkts encrypt: 21281, #pkts digest: 21281 #pkts decaps: 21281, #pkts decrypt: 21281, #pkts verify: 21281 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 21281, #pkts comp failed: 0, #pkts decomp failed: 0 #pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0 #PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0 #TFC rcvd: 0, #TFC sent: 0 #Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0 #send errors: 0, #recv errors: 0
packet-tracer での確認
ciscoasa# packet-tracer input inside icmp 192.168.10.100 0 8 192.168.20.100 Phase: 1 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: in 192.168.20.0 255.255.255.0 via 10.1.2.254, outside !...上記ルーティングテーブルにより転送されている事を確認 Phase: 2 Type: UN-NAT Subtype: static Result: ALLOW Config: nat (inside,outside) source static local-network local-network destination static remote-network remote-network no-proxy-arp route-lookup Additional Information: NAT divert to egress interface outside Untranslate 192.168.20.100/0 to 192.168.20.100/0 !...上記 NAT 設定により、暗号化対象のフローは NAT 対象外となっている事を確認 Phase: 3 Type: NAT Subtype: Result: ALLOW Config: nat (inside,outside) source static local-network local-network destination static remote-network remote-network no-proxy-arp route-lookup Additional Information: Static translate 192.168.10.100/0 to 192.168.10.100/0 <...snip...> Phase: 8 Type: VPN Subtype: encrypt Result: ALLOW Config: Additional Information: !...VPN により暗号化され、通信が許可されている事を確認 <...snip...> Result: input-interface: inside input-status: up input-line-status: up output-interface: outside output-status: up output-line-status: up Action: allow !...最終的に該当通信を許可している事を確認
VyOS 設定例
IKE ポリシーの設定
set vpn ipsec ike-group IKE-1W lifetime 86400 set vpn ipsec ike-group IKE-1W proposal 1 dh-group 2 set vpn ipsec ike-group IKE-1W proposal 1 encryption aes128 set vpn ipsec ike-group IKE-1W proposal 1 hash sha1
Phase2ポリシーの設定
set vpn ipsec esp-group ESP-1W lifetime 28800 set vpn ipsec esp-group ESP-1W mode tunnel set vpn ipsec esp-group ESP-1W pfs dh-group2 set vpn ipsec esp-group ESP-1W proposal 1 encryption aes128 set vpn ipsec esp-group ESP-1W proposal 1 hash sha1
インターフェースでの IPsec 有効化
set vpn ipsec ipsec-interfaces interface eth2
NAT-T 有効化
set vpn ipsec nat-traversal enable
IPsec ピアの設定
set vpn ipsec site-to-site peer 10.1.2.1 authentication mode pre-shared-secret set vpn ipsec site-to-site peer 10.1.2.1 authentication pre-shared-secret cisco set vpn ipsec site-to-site peer 10.1.2.1 default-esp-group ESP-1W set vpn ipsec site-to-site peer 10.1.2.1 ike-group IKE-1W set vpn ipsec site-to-site peer 10.1.2.1 local-address 10.1.1.2 set vpn ipsec site-to-site peer 10.1.2.1 tunnel 1 esp-group ESP-1W set vpn ipsec site-to-site peer 10.1.2.1 tunnel 1 local prefix 192.168.20.0/24 set vpn ipsec site-to-site peer 10.1.2.1 tunnel 1 remote prefix 192.168.10.0/24
設定の有効化と保存
commit save
IPsec 関連の最終設定
show | commands | grep vpn set vpn ipsec esp-group ESP-1W lifetime '28800' set vpn ipsec esp-group ESP-1W mode 'tunnel' set vpn ipsec esp-group ESP-1W pfs 'dh-group2' set vpn ipsec esp-group ESP-1W proposal 1 encryption 'aes128' set vpn ipsec esp-group ESP-1W proposal 1 hash 'sha1' set vpn ipsec ike-group IKE-1W lifetime '86400' set vpn ipsec ike-group IKE-1W proposal 1 dh-group '2' set vpn ipsec ike-group IKE-1W proposal 1 encryption 'aes128' set vpn ipsec ike-group IKE-1W proposal 1 hash 'sha1' set vpn ipsec ipsec-interfaces interface 'eth2' set vpn ipsec nat-traversal 'enable' set vpn ipsec site-to-site peer 10.1.2.1 authentication mode 'pre-shared-secret' set vpn ipsec site-to-site peer 10.1.2.1 authentication pre-shared-secret 'cisco' set vpn ipsec site-to-site peer 10.1.2.1 default-esp-group 'ESP-1W' set vpn ipsec site-to-site peer 10.1.2.1 ike-group 'IKE-1W' set vpn ipsec site-to-site peer 10.1.2.1 local-address '10.1.1.2' set vpn ipsec site-to-site peer 10.1.2.1 tunnel 1 esp-group 'ESP-1W' set vpn ipsec site-to-site peer 10.1.2.1 tunnel 1 local prefix '192.168.20.0/24' set vpn ipsec site-to-site peer 10.1.2.1 tunnel 1 remote prefix '192.168.10.0/24'
IPsec の確認
vyos@vyos02# run show vpn ike sa Peer ID / IP Local ID / IP ------------ ------------- 10.1.2.1 10.1.1.2 State Encrypt Hash D-H Grp NAT-T A-Time L-Time ----- ------- ---- ------- ----- ------ ------ up aes128 sha1 2 no 11316 86400 vyos@vyos02# run show vpn ipsec sa Peer ID / IP Local ID / IP ------------ ------------- 10.1.2.1 10.1.1.2 Tunnel State Bytes Out/In Encrypt Hash NAT-T A-Time L-Time Proto ------ ----- ------------- ------- ---- ----- ------ ------ ----- 1 up 1.7M/1.7M aes128 sha1 no 11319 28800 all
冗長試験
正常時
①ASA のフェイルオーバ状況を確認する。*2
ciscoasa# failover exec active show fail Failover On Failover unit Primary Failover LAN Interface: failover GigabitEthernet0/2 (up) Unit Poll frequency 1 seconds, holdtime 15 seconds Interface Poll frequency 5 seconds, holdtime 25 seconds Interface Policy 1 Monitored Interfaces 3 of 61 maximum Version: Ours 9.2(0)2, Mate 9.2(0)2 Last Failover at: 02:57:55 UTC Sep 19 2016 This host: Primary - Active <--- プライマリ(ASA01)が Active Active time: 12055 (sec) slot 0: empty Interface inside (192.168.10.1): Normal (Monitored) Interface outside (10.1.2.1): Normal (Monitored) Interface management (192.168.1.101): Normal (Monitored) Other host: Secondary - Standby Ready <--- セカンダリ(ASA02)が Standby Active time: 12455 (sec) Interface inside (192.168.10.2): Normal (Monitored) Interface outside (10.1.2.2): Normal (Monitored) Interface management (192.168.1.102): Normal (Monitored)
②CentOS01 から CentOS02 へ Ping を実行し、通信状況を確認する。
CentOS01の Ping 状況
# ping 192.168.20.100 -c 2 PING 192.168.20.100 (192.168.20.100) 56(84) bytes of data. 64 bytes from 192.168.20.100: icmp_seq=1 ttl=63 time=1.39 ms 64 bytes from 192.168.20.100: icmp_seq=2 ttl=63 time=1.45 ms <...snip...>
ASA でパケットキャプチャ
ciscoasa# capture capout interface outside match esp any any ciscoasa# show capture capout <...snip...> 1: 06:12:28.294433 10.1.2.1 > 10.1.1.2: ip-proto-50, length 132 2: 06:12:28.295227 10.1.1.2 > 10.1.2.1: ip-proto-50, length 132 <...snip...> ciscoasa# no capture capout interface outside match esp any any
故障時*3
①ASA のフェイルオーバ状況を確認する。*4
ciscoasa# failover exec active show fail Failover On Failover unit Secondary Failover LAN Interface: failover GigabitEthernet0/2 (up) Unit Poll frequency 1 seconds, holdtime 15 seconds Interface Poll frequency 5 seconds, holdtime 25 seconds Interface Policy 1 Monitored Interfaces 3 of 61 maximum Version: Ours 9.2(0)2, Mate 9.2(0)2 Last Failover at: 06:27:56 UTC Sep 19 2016 This host: Secondary - Active <--- セカンダリ(ASA02)が Active へ遷移 Active time: 40 (sec) slot 0: empty Interface inside (192.168.10.1): Normal (Monitored) Interface outside (10.1.2.1): Normal (Waiting) Interface management (192.168.1.101): Normal (Monitored) Other host: Primary - Failed <--- プライマリ(ASA01)が Failed へ遷移 Active time: 12567 (sec) Interface inside (192.168.10.2): Normal (Monitored) Interface outside (10.1.2.2): No Link (Waiting) Interface management (192.168.1.102): Normal (Monitored)
②CentOS01 から CentOS02 へ Ping を実行し、通信状況を確認する。
CentOS01の Ping 状況
# ping 192.168.20.100 -c 2 PING 192.168.20.100 (192.168.20.100) 56(84) bytes of data. 64 bytes from 192.168.20.100: icmp_seq=1 ttl=63 time=2.61 ms 64 bytes from 192.168.20.100: icmp_seq=2 ttl=63 time=12.6 ms <...snip...>
ASA でパケットキャプチャ
ciscoasa# capture capout interface outside match esp any any ciscoasa# show capture capout <...snip...> 1: 06:32:43.445243 10.1.2.1 > 10.1.1.2: ip-proto-50, length 132 2: 06:32:43.446067 10.1.1.2 > 10.1.2.1: ip-proto-50, length 132 <...snip...> ciscoasa# no capture capout interface outside match esp any any
参考:
Configure a Site-to-Site IPSec IKEv1 Tunnel Between an ASA and a Cisco IOS Router
IPSec Tunnel from ASA55xx to VyOS (or Vyatta)
packet-tracerを用いたトラブルシューティング
以上