WordPress をはじめました
WordPress をはじめました。
はてなブログも引き続き書いていきたいと思いますが、更新頻度は落ちてしまうかもです。
落ち着いたら、はてなブログと WordPress の比較なども書きたいと思います。
過去の記事の一部は WordPress に移行予定です。
まだ始めたばかりですが個人的な所感としては、以下の点ではてなブログのメリットは大きいなと感じています。
はてなブロガーの皆さんと交流できる
個人的にはこれが一番大きいです。スターを1つつけてもらうたびにモチベーションが高まりますし、記事を書くのが楽しくなります。
記事に集中できる
便利な機能が実装されていてメンテナンスもはてなさんが対応してくれるため、記事を書くことに集中できます。
WordPress はプラグインをいれたり、それらをアップデート・管理する必要があるため結構大変です。
SEO に強い
WordPress の方が強いという記事もちらほら見かけますが、サーチコンソールやアナリティクスで解析してみてもはてなブログの SEO はかなり高いです。
まだ、WordPress をはじめて間もないのであくまで所感ですが、同じ品質の記事ならはてなブログの方が強いような気もします。
以上、今後は WordPress の良い点についても共有できればなと思います。
最後までお読み頂きありがとうございました。
Windows Defender をおすすめする理由
Windows 10 におけるウィルス対策ソフトは色々とありますが、個人的には費用対効果の観点から Windows Defender がおすすめです。理由は無料で十分な防御力があるからです。
以前はそれほどでもなかったのですが、最近はかなり改善されているように見えます。
AV-Comparatives*1 の最新の Real-World Protection Test の結果を見ても、市販の製品と比較して大差はないように思います。
Real-World Protection Test とは
ウイルス対策ソフトがどの程度ウィルスから保護できるか近似環境で確認するテストです。
以下は 2021年2月~3月のテスト結果で AV-Comparatives 様の許可のもとに掲載しています。
- Compromised:攻撃を防げなかった割合
- User dependent:攻撃を防げなかったが設定で防げる割合
- Blocked:攻撃を防いだ割合
- False Positive:誤検知(正常なファイルをウィルスと判断した)割合
「Micorosoft」が Windows Defender になります。攻撃を防いだ割合は 95% 以上あり、誤検知も少ないため十分に利用できる性能と考えます。
なお、コストを考慮せず防御力を重視する場合は、個人的には Trend Micro 社の「ウイルスバスター」がおすすめです。
セキュリティに100%はなく多層防御が基本となることから、ウィルス対策ソフト(無料・有料)に関わらず定期的な Windows Update 実施や、不審なファイルを実行しないことが重要です。
以上
*1:ウイルス対策ソフトウェアをテストおよび評価するオーストリアの独立組織
HP ENVY(AMD)でプチフリーズ
HP ENVY x360 15-ee(AMD)で、操作中にプチフリーズする事象がありました。マウスやキーボード操作中に一瞬(1秒~5秒程度)画面が固まって操作不可となります。
原因はわかりませんが、私の場合、以下を実施することで解決しました。
McAfee LiveSafe のアンインストール
McAfee が悪さをしているという情報がちらほらあったので、試してみました。
McAfee の代わりになるアンチウィルスソフトですが、個人的には Windows Defender が推奨です。
McAfee LiveSafe のアンインストール方法はこちら
CCNA の勉強方法
ネットワークエンジニアが最初に目指す資格として有名な CCNA を勉強する際、参考になりそうなサイトや書籍等を紹介します。
CCNA イージス
CCNA イージスとは
CCNA イージスとは、CCNA の Web 教科書のことです。CCNA イージスには CCNA(200-301)の試験範囲の全ての技術解説があり、CCNA イージスだけで CCNA に合格するためのネットワーク技術力が身につけることができます。また、NW エンジニアの仕事で必要な技術を体系的に解説しており資格試験だけでなく実際の仕事でも役立ちます。
出典:CCNA イージス
おすすめのポイント
市販の CCNA 教科書と同レベルの内容を無料で提供してくれています。こちらと市販の問題集を併用すれば、合格率はかなり高くなると思われます。
市販の問題集でおすすめは以下になりますが、「Ping-t」の無料問題集でもある程度カバーできると思います。
Ping-t
Ping-t とは
CCNA/CCNP、LinuC、LPIC、HTML5プロフェッショナル認定資格、OSS-DB、オラクルマスター、ITパスポート、 ITILファンデーション試験の合格を目指す人を応援する学習サイトです。(登録ユーザ数25万人超)
出典:Ping-t
おすすめのポイント
ユーザー登録をすると無料で問題集「CCNA(200-301)(400問)」をもらえます。また、「助け合いフォーラム」で質問もできます。市販の問題集を使わない場合の選択肢にはいると思います。
その他
ネットワークの基礎技術の習得および CCNA 取得には基本的には上記で十分*1だと思いますが、短期間で体系的に学びつつ、手厚いサポートが受けられる手段として IT スクールという選択肢もあります。
有名な IT スクールとしては「ウズウズカレッジ CCNA コース」があり、以下のような方におすすめです。
- 短期間(1カ月)でネットワーク 基礎技術の習得および CCNA を取得したい。
- 個別にしっかりと丁寧に指導してほしい。
- CCNA 取得後の就職(転職)のサポートをしてほしい。
以下、注意点です。
- 受講費用 165,000円(税込)・3ヶ月分の料金がかかります。他の IT スクールと比較してリーズナブルではありますが、それなりの費用がかかるため、事前にしっかりと確認することをおすすめします。
- 無料体験はありません。ただし、無料説明会があるので雰囲気や様子などは質問できると思います。
以上
*1:あくまで個人の感想なのでご参考まででお願いします。
STP の概要
STP とは
STP(Spanning Tree)は、 冗長経路によるループを検出し、フレームの送受信を停止させることにより、ループフリーのネットワークを形成する機能です。
- IEEE 802.1d として標準化
- Configuration BPDU と呼ばれるフレームを使用して、Topology 情報を共有する。
- Root Bridge を起点とする Active Topology と呼ばれる Tree Topology を構成する。
詳細が知りたい場合は、「スパニングツリーの概要 | ネットワークエンジニアの小学校」がわかりやすく、おすすめです。
Active Topology の形成と維持
- BPDU の優劣に応じて、Root Bridge / Forwarding / Blocking ポート等を決定する。
- 機器及び、リンク故障時の切替えには、約30~50秒要する。
正常時

故障時

BPDU について
BPDU(Bridge Protocol Data Unit)は、Active Topology の作成、維持、管理を行うためのフレームで以下の特徴があります。
- スイッチ間でデフォルトでは、2秒間隔で送信、交換
- BPDU には 「Configuration BPDU」 と「Topology Change Notification BPDU」の 2 種類が存在
BPDU のフォーマット

参考書籍
その他参考
以上
VLAN の概要
VLAN とは
VLAN(Virtual LAN)とは、スイッチ内でブロードキャストドメインを分割する機能で、主な利点は以下の 2つです。
- 異なる VLAN 間の通信はできなくなり、セキュリティの向上が図れる。
- ブロードキャストドメインを狭めることで、帯域を有効活用できる。
図にすると、次のような感じです。
VLAN10 や VLAN20 の「数字」は、VLAN ID と呼ばれる識別番号です。

VLAN10 に設定したポートにはいってきたフレームは、同じく VLAN10 を設定したポートにしか転送されません。
Cisco で GE0/1 を VLAN10 に指定する場合は、次のように設定します。
Switch#configure terminal Switch(config)#interface gigabitethernet0/1 Switch# (config-if)#switchport mode access Switch# (config-if)#switchport access vlan 10
VLAN トランクとは
- 複数の VLAN トラフィックを1つの物理リンク上で伝送する技術
- Cisco は、IEEE 標準の「802.1q」と Cisco 独自仕様の 「ISL(Inter-Switch Link)」をサポート
- 802.1q 及び ISL は、それぞれ、タグと呼ばれる識別子をフレームに挿入し、複数の VLAN データを 1つのリンクで送受信できるようにします。

Cisco で GE0/24 をトランクポート(VLAN10,20)に指定する場合は、次のように設定します。
Switch#configure terminal Switch(config)#interface gigabitethernet0/24 Switch# (config-if)#switchport mode trunk Switch# (config-if)#switchport trunk allowed vlan 10,20
参考書籍
その他参考
以上
はてなブログでよく使うシンタックスハイライト
ブログを書く時に使っているシンタックスハイライトの覚書です。
シンタックスハイライトとは
可読性を上げるため、ソースコードを色付けして表示する機能です。
はてな記法とシンタックスハイライト
はてなブログでシンタックスハイライトを使用するためには、スーパー pre 記法で先頭の >|| の 2本のパイプ(||)の間に指定します。
シンタックスハイライトの使用例
で書かれたソースコードの場合、以下のように html と書きます。
>|html| <html> <head> <title>NETWORK ENGINEER BLOG</title> </head>
次のようにハイライトされます。
<html> <head> <title>NETWORK ENGINEER BLOG</title> </head>
よく使うハイライト
config:Cisco などの Config 関連sh:Linux などの Shell 関連ps1:PowerShell 関連python:Python 関連yaml:YAML 関連html:HTML 関連sql:SQL 関連
おまけ
余談ですが、はてなブログでソースコードの一部(configなど) を表示する場合は、以下のようにHTML の code タグを使用しています。
-<code>config</code>
すごくめんどくさいので、簡単にかける方法があれば教えてください。。
参考書籍
以上
HTML の基本について
HTML とは
HyperText Markup Language(ハイパーテキスト マークアップ ランゲージ)は、ハイパーテキストを記述するためのマークアップ言語の 1 つ。略して HTML(エイチティーエムエル)と呼ばれることが多い。…(中略)…フォントや文字色の指定などの見た目の指定、などといった機能がある。
出典:フリー百科事典『ウィキペディア(Wikipedia)』
ちょっと何言ってるか分からない。「ハイパーテキスト」って何だろう。
ハイパーテキストとは
ハイパーテキスト (hypertext) とは、複数の文書(テキスト)を相互に関連付け、結び付ける仕組みである。「テキストを超える」という意味から"hyper-"(~を超えた) "text"(文書)と名付けられた。テキスト間を結びつける参照のことをハイパーリンクと言う。…(中略)…最も有名なハイパーテキストの実装は World Wide Web である。
出典:フリー百科事典『ウィキペディア(Wikipedia)』
一言でいうと HTML は Web ページを書くための言語ということみたいです。
HTML の書き方
文章を「タグ」と呼ばれるもので囲って(マークアップ=目印をつけて)書いていきます。
なんでものびる WEB さんの説明がわかりやすかったので、引用させて頂きます。
出典:なんでものびる WEB
上記のように、開始タグ <>と 終了タグ </> で囲って書いていきます。
囲まれた文章は、「<タグの名前>要素」と呼ばれます。
主な HTML タグについて
<html></html>:HTML 文書であることを宣言
<head></head>:文書のヘッダを指定
<title></title>:文書のタイトルを指定
<body></body>:文書の本文を指定
<p></p>:段落を指定
<h1~6></h1~6>:文書の見出しを指定(h1 が最も大きく、h6 が最も小さい)
出典:なんでものびる WEB
他にも様々なタグがあります。以下は HTML5 のタグの一例です。詳細はこちら
<img></img>:画像からファイルを読み込む
<strong></strong>:文字を太字にする。
<a></a>:ハイパーリンクを指定※
※アンカータグとよばれ、以下のように記述します。
<a href="sample.html" title="これはリンクです" target="_blank">
HTML の例
上記の HTML タグを使った例です。
<html> <head> <title>NETWORK ENGINEER BLOG</title> </head> <body> <h1>HTML の書き方</h1> <h2>主な HTML タグについて</h2> <p>HTML タグには、たくさん種類があります。</p> <p>アンカータグを使えば、<a href=https://friendsnow.hatenablog.com/ target=”_blank”>リンク</a>を挿入することもできます。 </body> </html>
上記のソースコードを HTML でみると以下(右側)のように表示されます。

以上
定期的なパスワード変更が不要になった理由
「いまだに、定期的にパスワード変更を求めるサービスが結構あるね。」という話を、CSIRT 業務経験のある妻に話したところ、「(パスワード)盗難対策として、必要だからじゃない?」という回答だったので、結構前に不要になった話をしました。
とても驚いていたので、ドヤ顔で講釈をはじめたのですが、うっとおしがられて聞いてもらえなかったので、こちらに書きます。
総務省の方針転換
過去、パスワードを盗難対策として、「定期的なパスワード変更は必要」とされていたのですが、2018年3月に総務省が「不要」と方針転換を発表しました。
簡単にいうと、「パスワードを定期的に変更すると、単純なものを設定したり、使いまわしたりしがちであるから」というのが理由です。
なお、利用するサービスによっては、パスワードを定期的に変更することを求められることもありますが、実際にパスワードを破られアカウントが乗っ取られたり、サービス側から流出した事実がなければ、パスワードを変更する必要はありません。むしろ定期的な変更をすることで、パスワードの作り方がパターン化し簡単なものになることや、使い回しをするようになることの方が問題となります。定期的に変更するよりも、機器やサービスの間で使い回しのない、固有のパスワードを設定することが求められます。
これまでは、パスワードの定期的な変更が推奨されていましたが、2017年に、米国国立標準技術研究所(NIST)からガイドラインとして、サービスを提供する側がパスワードの定期的な変更を要求すべきではない旨が示されたところです*1。また、日本においても、内閣サイバーセキュリティセンター(NISC)から、パスワードを定期変更する必要はなく、流出時に速やかに変更する旨が示されています*2。
出典:総務省
逆に言えば、複雑なパスワードを使いまわさず設定するなら、「盗まれても利用される期間が短くなる」といった観点で考えても、有効な対策かもしれません。
パスワードは複雑なものを推奨
定期的に変更するよりも、推測されにい長くて複雑なパスワードの設定が推奨されています。
最近は、コンピューターの処理性能が飛躍的に向上したため、攻撃者は短時間で多くのパスワードを試行できます。*3
また、どれだけ長くて複雑にしても、今後さらにコンピューターの性能が向上した場合に解析される恐れがあるので、試行回数の制限や、二要素認証はしっかりと実装しておく必要があります。
参考書籍
以上
*1:NIST SP800-63B(電子的認証に関するガイドライン)
*2:https://www.nisc.go.jp/security-site/handbook/index.html
*3:いわゆる総当たり攻撃やパスワードリスト攻撃
息子の難病と仕事の変化
振り返りを兼ねて、書いてみます。
息子がクローン病と診断
息子が 3 歳の時、「潰瘍性大腸炎」と診断され、漢方治療で 4 年ほど症状が治まっていましたが、徐々に容体が悪化し、昨年7月に再検査をした結果、「クローン病」と診断されました。
クローン病と潰瘍性大腸炎は、慢性の炎症性腸疾患の一つであり、腹痛や下痢、発熱といった症状を伴います。
大きな違いは、潰瘍性大腸炎は大腸だけに炎症が起こりますが、 クローン病は消化管のどの位置にも炎症を起こす可能性があります。
最初の治療は、エレンタールと呼ばれる総合栄養剤以外は絶食(4週間)という過酷なものでした。
入院中、「食べたい食べたい」と泣きじゃくる息子の姿は、今でも脳裏に鮮明に焼き付いています。
食事再開後も、炎症が再発するなど、しばらく辛い状況が続きましたが、今はレミケードというお薬を定期的に点滴することで、寛解を維持することができています。
先生やスタッフの皆様には、なんとお礼を申し上げてよいのか・・感謝の言葉もありません。
また、食事にはものすごく気をつけなくてはならないため、毎日試行錯誤しながら料理を作ってくれている妻に感謝しています。

テレワーク中心の生活
COVID-19 の影響で、テレワークが中心となりました。
コミュニケーションは、ビデオ会議や、チャットツールがメインとなり、意思疎通が図りづらい日々が続いています。
姿が見えないことへの不安はもちろん、表情や言葉で得られる情報は多かったのだと痛感しています。

一方で、通勤時間が減った分、時間を確保できて、ブログを書いたり、子供と遊ぶ時間が増えたという側面もありました。
息子の影響で、ポケモンカードゲームをはじめたのですが、今では自分が夢中になってしまい、大人の財力で箱買いして、大人げなく全力で戦っています。(でもなぜか負け越しています。奥が深いゲームです。。)
気持ちの変化
息子の闘病生活において、笑顔を支えてくれたのが、ポケモンカードやニンテンドースイッチなどのエンタメでした。
以前から興味はありましたが、息子の影響でより強くなり、これまでインフラ一筋の仕事をしてきましたが、今のエンタメ系コンテンツ開発の仕事に踏み出すきっかけとなりました。
自分もできるだけ多くの人へ笑顔を届けられるような、そんなコンテンツを開発できればと思っています。
また、これまで培ったインフラの知識を、少しづつにはなりますが、はてなブログで共有し、恩返しができればと思います。
以上です。ここまで読んで頂きありがとうございました。
openSUSE Tumbleweed の XRDP で画面が真っ黒になる
Windows 10 から、openSUSE Tumbleweed に XRDP で接続した際、以下のように、画面が真っ黒になる問題に遭遇しました。

原因は「同じユーザーで、ローカル接続していること」でした。
以下のコマンドで、対象ユーザーの全プロセスを kill すると解決しました。
hostname:~# killall -u USERNAME
参考書籍
以上
Windows 10 から openSUSE Tumbleweed に XRDP 接続
openSUSE ソフトウェアで「XRDP」を検索し、openSUSE Tumbleweed の「1クリックインストール」をクリックしてインストールします。
XRDP 接続設定
XRDP を有効化
hostname:~# sudo systemctl enable xrdp
XRDP を起動
hostname:~# sudo systemctl start xrdp
Firewall ポート許可
hostname:~# sudo firewall-cmd --add-port=3389/tcp --permanent
Firewall 再起動
hostname:~# sudo firewall-cmd --reload
接続方法
RDP 接続すると、XRDP が起動するので、Session に「Xvnc」に指定し、 ユーザー名とパスワードを入力後、「OK」をクリックします。

XRDP で接続可能となります。

参考書籍
以上
はてなブログに Google アナリティクス 4 プロパティを設定
はてなブログに Google アナリティクス 4 プロパティ(GA4)を設定する方法です。
Google アナリティクス 4 プロパティとは
Google アナリティクス 4 プロパティ(GA4)はアプリ計測ツール「Google アナリティクス For Firebase」の仕組みを土台として、データ構造から再設計された新しい Google アナリティクスです。2019年に発表された「アプリ+ウェブ プロパティ」が、正式に2020年10月に β 版から名称を「Google アナリティクス 4 プロパティ(GA4)」へ変えてリリースされました。
…(中略)…
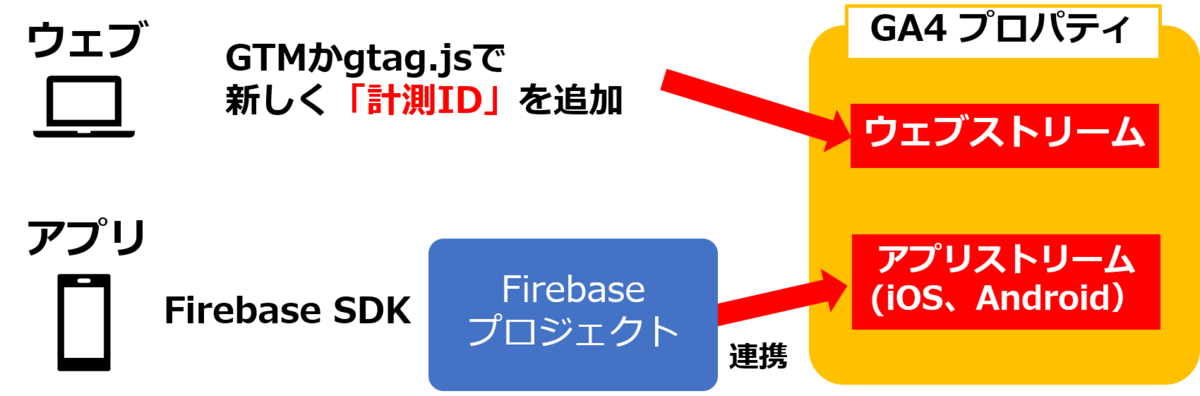
Google アナリティクス 4 プロパティはプロパティの中に「データストリーム」という新しい概念が追加されました。データストリームは「ウェブ」「iOS」「Android」とそれぞれのデータストリームに分かれています。
ウェブは「GTM か gtag.js で新しい計測 ID をウェブサイトへ追加」することでGA4プロパティの「ウェブストリーム」にデータを収集することができ、iOS、Android は「Firebase プロジェクト」と Google アナリティクス 4 プロパティを連携することで「アプリストリーム」にデータを収集することができます。
出典:アユダンテ株式会社
はてなブログ設定方法
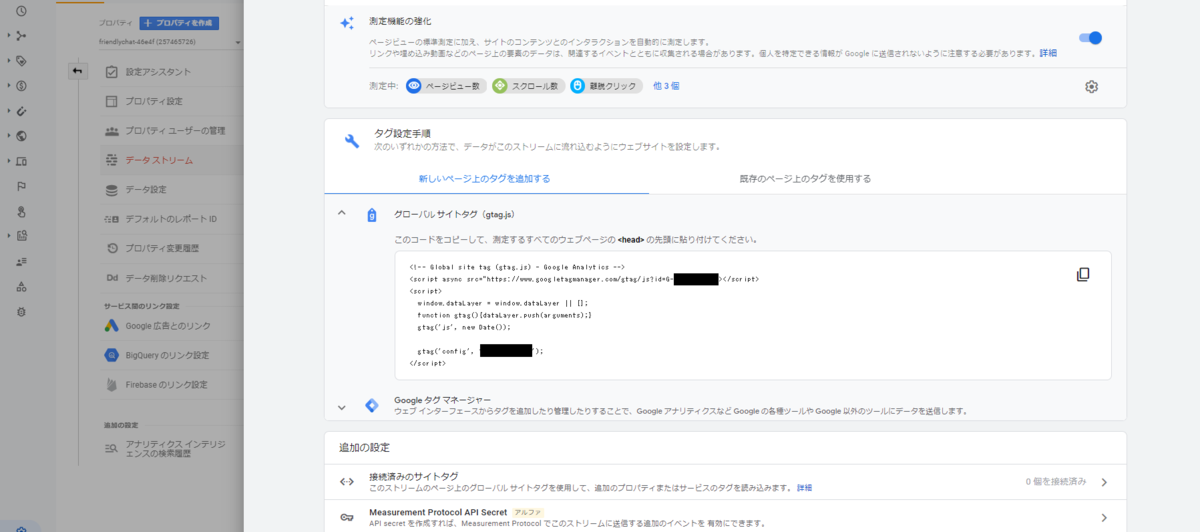
- GA4 に接続して、左ペインの「管理」➡「データストリーム」をクリックします。
- グローバルサイトタグ(gstag.js)をコピーして、はてなブログの「設定」➡「詳細設定」の「head に要素を追加」に貼り付けます。
しばらく経過すると、測定結果が反映されます。
以上
デュプレックス(duplex)について
全二重(Full-duplex) 半二重(Half-duplex)とは
- 半二重モードでは、送信と受信を片方向ずつ、時間を分けて通信する。
- 100BASE-TX の場合、送信と受信あわせて、最大100Mbps の通信が可能。
- 全二重モードでは、送信と受信を両方向同時に通信する。
- 100BASE-TX の場合、送信と受信それぞれ最大 100Mbps の通信が可能。
- HUB は CSMA/CD 方式である半二重モードのみをサポートしており、送受信を同時に行えない。

オートネゴシエーションについて
- FLP(Fast Link Pulse)バーストと呼ばれるパルス信号を使用し、互いの通信速度とモードを検出する。
- 相互の通信モードによっては、リンクダウンや、半二重通信になってしまう場合があるので、注意すること。
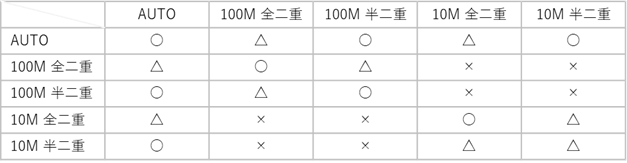
デュプレックスミスマッチについて
対向でデュプレックスがあっていない場合、デュプレックスミスマッチとなり、通信が正常にできない場合があります。
Cisco の場合は、CDP が有効になっていると、以下のエラーが出力されます。
%CDP-4-DUPLEX_MISMATCH: duplex mismatch discovered on FastEthernet0/1 (not full duplex), with R1 Ethernet0/0 (full duplex).
上記の表の「〇」となるように、対向の設定をあわせることが対策となります。
以上
Amazon RDS のパラメータ変更について
Amazon RDS(MySQL)において、パラメータグループを変更する際、以下のエラーが発生しました。
保存中のエラー: Cannot modify a default parameter group. (Service: AmazonRDS; Status Code: 400; Error Code: InvalidParameterValue; Request ID: xxxx-xxxx-xxxx-xxxx; Proxy: null)
原因は「デフォルトのパラメータグループの変更しようとしたこと」でした。
仕様上、デフォルトのパラメータグループは、変更不可のようです。
対策は、パラメータグループの作成になります。
パラメータグループの作成
パラメータグループを作成します。作成したパラメータグループは、設定変更が可能です。
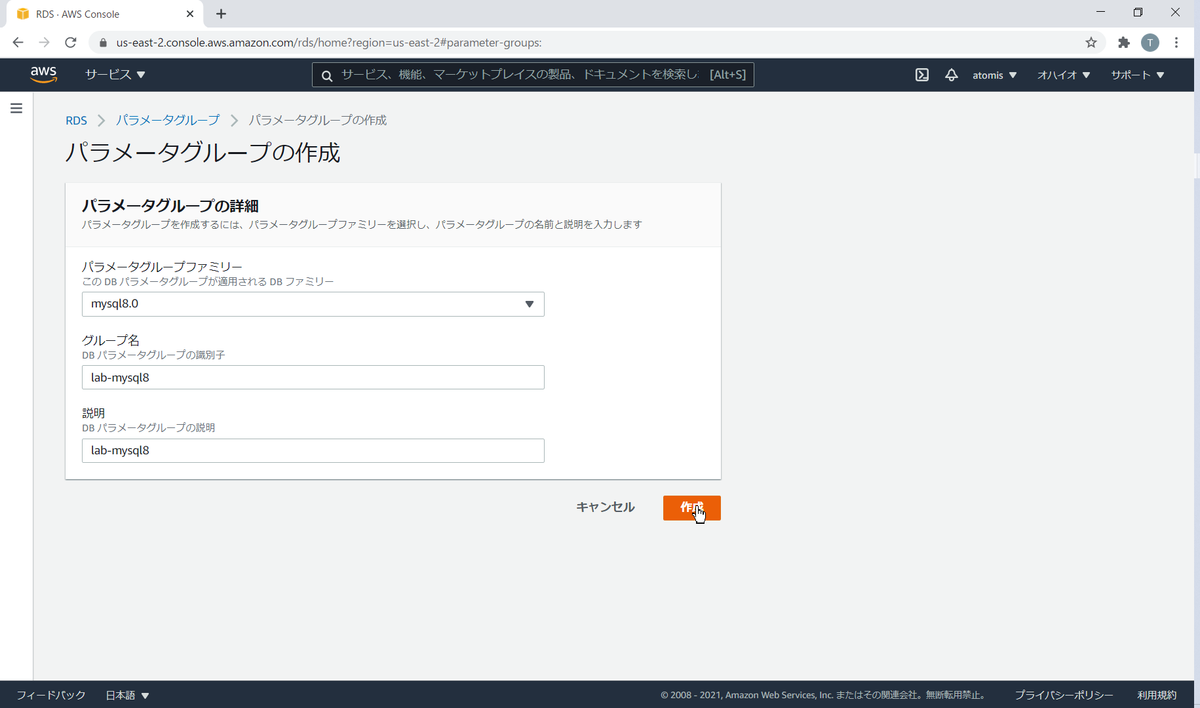
パラメータグループの適用
パラメータグループをデータベースに割り当てます。
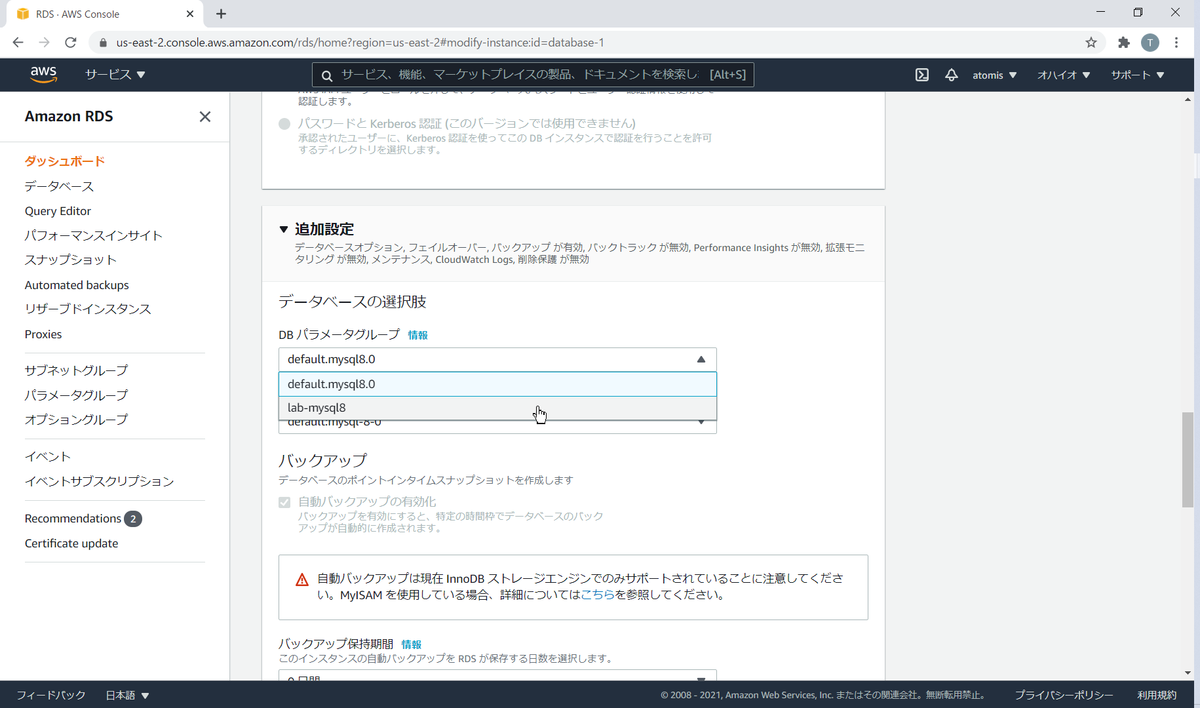
参考書籍
以上